GET Current trends in the development of DDoS attacks and protection against them using DefensePro Radware / MUK Blog / Sudo Null IT News FREE

Now, when the political and economic tensions in the countries are growing, the data war has long been in full swing on the Internet and in one of the first places are fit-known DDoS attacks.
Foremost, they are exposed to state and news web-resources, which to i degree or some other highlight current events not only in the aforementioned countries, but also around the world as a whole.
Let's take a nearer look at which DDoS attacks are in real time becoming the near popular and their growing trends in subsequent old age. Nether habrakat, my thoughts happening attacks and an overview of the Radware tribute solution
Increasing the number of vectors in DDoS attacks
The 1st thing that differs from DDoS attacks of 2013/2014 from the previous ones is that several vulnerability vectors are used. Since only one transmitter is adequate to bang the fair game and cause the sequent damage, this is why the probability of an attack's winner increases if you use galore vectors in one attack. To boot, such tactics confuse the IT personnel of the attacked organization.
Considering DDoS attacks arsenic a whole, in 2014 attacks aimed at web resources will continue to prevail as the fastest vector. Since 2013, there has been a clear increase in DDoS attacks on applications as a result of the presence of protection systems against meshing DDoS attacks deployed in recent years in organizations, as shown in Figure 1. In addition, network attacks are untold easier to resist, and they have never been categories of heavily deflected attacks.
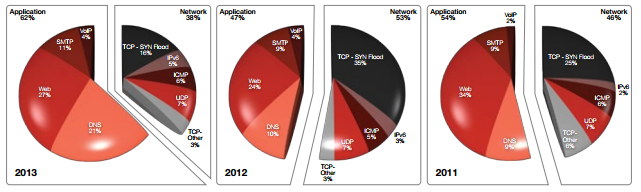
Fig. 1. Percentage distribution of DDoS attack vectors from 2011 to 2013
As mentioned above, many a means of repelling attacks have developed sufficiently and organizations stern stand DDoS attacks aimed at the network and applications for quite some time without flexible the Information technology infrastructure. But attackers can utilization many attack vectors to search for those that are not provided for by DDoS attacks mirror image solutions deployed in the organization. More than half of the cases are DDoS attacks with 5 or more vectors, A shown in Frame 2.
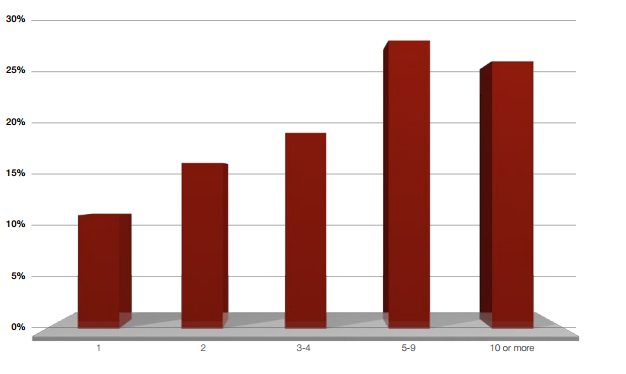
Fig.2. Numerate of attack vectors used in one DoS / DDoS attack campaign
Very often, attackers leave non use the entire armory at once, allowing the dupe to cognitive process attack vectors consecutive. When one attack vector is out of use, the attacking attacker leave set in motion the next. During a massive set on, an organization can block four operating theatre five attack vectors, but there will be one attack transmitter that cannot be repelled and cause add damage.
The objectives of modern DDoS attacks
In most cases, the result of a DDoS attack is a web server that is idle OR responding slowly. But in fact, DDoS attacks are aimed non only at web servers. The image under shows the main objectives of a DDoS set on - this is an Internet channel, likewise as a firewall. Chassis 3 below shows all network components that are subjected to DDoS attacks.
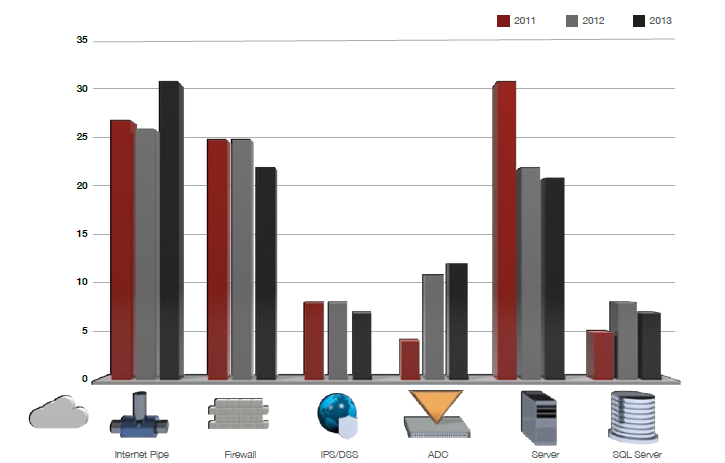
Fig. 3. Attacked Network Components
The periods between attacks are importantly reduced.
It's no secret that the assaultive side and selective information security experts play a ceaseless game of cat and mouse. This is an infinite call up: attackers develop new attacks, security experts develop countermeasures, and attackers, in good turn, invent new methods to bypass defense systems.
But in 2013-2014, the cycles of invention of new methods of bypassing protection systems were significantly reduced. One of the main vectors that led to this is HTTP flood attacks. They begin when the attacker sends a large number of Hypertext transfer protocol GET / Brand requests, depleting server resources.
SSL attacks continue to threaten organizations
Although HTTP attacks remain the most average, SSL encrypted attacks are still precarious because they are hard to resist.
Fraud, hacking, and a mindful list of privacy requirements have led organizations to use the HTTPS protocol and encrypted communications aside default. Reported to a telephone number of market studies, more than 90% of enterprises use HTTPS for any publicly accessible web fundamental interaction. Typically, HTTPS messages are decrypted at a very late present inside the brass's network. This is shown in Figure 4, where the decryption takes come in on a load balancer, low inside the organization's network.

Libyan Islamic Fighting Group. 4. Bypass organization security measur systems using SSL-encrypted DDoS attacks
Attackers use this encrypted subject matter feature film As a technique to get around security solutions (anti-State / DDoS, firewall, and IPS / IDS), which finally remain blind to attack. This can be suggested by moving the SSL termination functionality to the perimeter of the establishment's network. However, such a solution can lead to distortion of network partitioning, since the concept of network segmentation is critical to meet the requirements of various safety standards, such as PCI-DSS. Likewise, network segments that deal with sensitive data can exist nonexempt to stringent restrictions and audits.
Another newsworthy feature supported SSL Department of State / DDoS attacks is the asymmetric nature of SSL encryption, the peculiarity of which is that decrypting a message takes just about 10 times more resources than encrypting it.
Victimisation this asymmetric have, attackers can create a very destructive attack with relatively low resources. Using the methods of bypassing security measures systems represented above, the assailant, using peculiar tools, is able to fork up malicious messages deep into the network, where servers and various modules are more vulnerable to high traffic to observe unsatisfactory delays or a all-out shutdown. SSL-encrypted attacks is a new trend that will increase over the years and according to forecasts in 2017, more than half of DDoS attacks leave be SSL-encrypted.
You can continue to continue for a long time about the trends of cybercriminals in the field of DDoS attacks, which will greatly increase the article, but let's look at solutions that can resist them.
Product Overview DefensePro Radware as a way of life to protect against modern DDoS attacks
The DefensePro organization combines standard IPS and automatic protection against DDoS attacks in one result, which plant without operator interference when repelling an attack. Distinctive features are high performance (an plan of attack can reach 25,000,000 packets per second, and automatically beats off in 18 seconds!) And no damage to legitimate users during an onrush. In devices of the entire DefensePro line, hardware quickening of network traffic occurs ascribable specialized ASIC and FPGA processors.
The model range includes devices without built-in IPS, as swell as with constitutional IPS, which for the most part relies connected a luxuriously-performance context of use processor for hardware acceleration of signature analysis of net packets.
Network traffic is processed little by little exploitation individual shelter mechanisms. At the same time, the tote up network parcel delay time for altogether DefensePro rulers does non exceed 60 microseconds. Radware DefensePro's
intrinsical protection mechanisms are Eastern Samoa follows: • Behavioural DDoS Protection • TCP SYN Alluvion Auspices • Connection Circumscribe • HTTP Mitigator • Behavioral Server-Bang-up Protection • Bandwidth Direction • Key signature Protection • Stateful Inspection • Opposing-Scanning Engine Protection • Stateful Firewall (ACL) Also free actions: • Drop mailboat • reset (source, destination, both)
• suspend (source, src port, destination, destination port or any combination)
• Challenge-Response for HTTP and DNS attacks
Advantages of DefensePro - this is primarily the possibility of a licensed growth in productivity as required without replacing equipment, fillet the service without any reconfiguration devices. Also, DefensePro comes with a level of technical patronize, which includes assist from the ERT (Emergency Response Team) team up from Radware. This team is a radical of specialists who, just in case of enceinte DDoS attacks, connects to the gimmick and performs period dominance to repel the attack.
Another important advantage of RadwareDefensePro is a service for redirecting all incoming traffic during a DDoS attack that exceeds the bandwidth of the company's Net channel to the Radware cloud, after which already cleared dealings returns to the formation. This service is named Defense Pipe, and its operation is clearly shown in Figure 5.
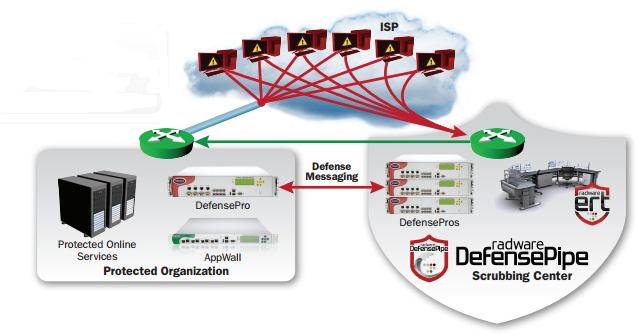
Figure 6. Redirecting all traffic during a DDoS snipe that exceeds the bandwidth of the Internet canalise to the Radware cloud for cleansing
The Radware DefensePro gimmick line consists of the following series:
• x420

• x412

• x16

• x06

Successively, each series of devices includes some models, which are shown in Figure 6.

Fig.6. Radware DefensePro product channel
In total, DDoS attacks have been and will be in the sexual climax years the most popular tool around for causing profitable damage from the downtime of online services, as well every bit for lowering the report of political groups by denying the table service of constituted websites. These attacks accepted a special growth growth with increasing political tension in the world, which makes them more sophisticated and unpredictable. All of the above factors make organizations Sooner or afterward consider the topic of acquiring protection systems against much attacks. In Holy Order not to suffer financial losses and not lose persuasion repute in the modern extremely competitive world.
Contact info
For all questions radware@muk.ua
MUK-Service - all types of Information technology stamping ground: warranty, non-warranty mend, sale of spare parts, contract service
DOWNLOAD HERE
GET Current trends in the development of DDoS attacks and protection against them using DefensePro Radware / MUK Blog / Sudo Null IT News FREE
Posted by: thompsonusen2002.blogspot.com
0 Response to "GET Current trends in the development of DDoS attacks and protection against them using DefensePro Radware / MUK Blog / Sudo Null IT News FREE"
Post a Comment